Micropayments policy and Sustainability – Eco-Friendly Initiatives
Micropayments have emerged as a promising solution to drive sustainable practices and promote eco-friendly initiatives. The concept of micropayments involves facilitating small financial transactions for goods, services, or content, often as low as a few cents, which can be accumulated over time to support larger causes. Leveraging micropayments in sustainability efforts can have a profound impact on several fronts. Firstly, micropayments allow consumers to make environmentally conscious choices without straining their budgets. By breaking down costs into tiny increments, consumers are more likely to engage in green practices, such as opting for sustainable products or supporting carbon offset programs. For instance, they could easily contribute a few cents each time they purchase an eco-friendly product, generating a steady stream of funds to support businesses committed to reducing their carbon footprint. In conclusion, micropayments have the potential to revolutionize sustainability and eco-friendly initiatives by providing an accessible, scalable, efficient means of funding.
From empowering consumers to make green choices without financial strain, incentivizing businesses to adopt sustainable practices, and supporting community-based projects, these tiny transactions can add up to substantial positive change. The transparency and education aspects further enhance engagement and commitment to sustainability causes. Secondly, implementing micropayments policy for sustainable initiatives incentivizes businesses to adopt eco-friendly practices. Companies that make environmentally responsible decisions can be rewarded with these incremental payments from their customers, encouraging them to invest further in green technologies, renewable energy sources, and sustainable production methods. This financial motivation aligns profit motives with ecological responsibility, fostering a sustainable business culture. Furthermore, micropayments can play a crucial role in funding community-based sustainability projects. Local initiatives focused on planting trees, cleaning up oceans, or creating green spaces often face financial constraints.
By adopting micropayment systems, individuals can effortlessly contribute to these projects, enabling communities to drive sustainable changes on a grassroots level 소액결제 정책. The cumulative impact of numerous small contributions can translate into substantial funding for transformative eco-friendly endeavors. In addition to their financial benefits, micropayments for sustainability can promote awareness and education. Many micropayment platforms offer transparent tracking, enabling users to see exactly how their contributions are making a difference. This level of transparency fosters a sense of accountability and encourages individuals to stay engaged in the cause. Moreover, it presents an opportunity for educational campaigns, sharing the positive environmental outcomes achieved through micropayments and inspiring others to participate in the movement. Critically, micropayments also tackle one of the biggest challenges faced by traditional fundraising methods – transaction fees. With conventional payment systems, a significant portion of each donation often goes towards payment processing, reducing the actual funds available for the cause. Micropayment platforms, designed to handle numerous small transactions, can drastically minimize transaction fees, maximizing the impact of each contribution.





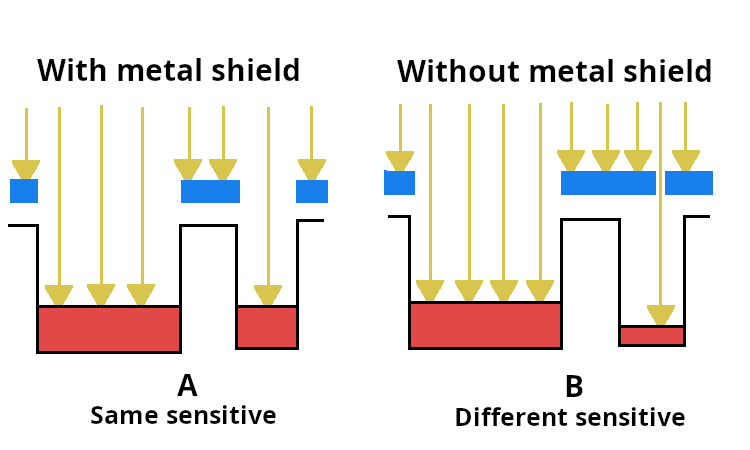 All these alterations impact the entire importance chain and that includes details service providers inside the field. Eurasia Photodiode semiconductor has been delivering information and facts to the global photodiode semiconductor market in excess of twenty five years. The adjustments from the international business signifies EuroAsia Photodiode semiconductor will yet again relocate in accordance with the photodiode semiconductor sector as it enters the following dynamic period of worldwide development. Silicon Photodiode semiconductor could be the new reputation for our name highlighting the easy actuality from the progressive engineering and manufacturing that identifies this world-wide business. The photodiode semiconductor market is tipped for powerful growth across the following few years and Silicon Photodiode semiconductor would be the essential information and facts portal for your world’s silicon photodiode semiconductor community, allowing positive interaction ways to foster advancement. The new headline also provides together our secure of titles, with the sister distribution Substance Photodiode semiconductor covering up production on substance material substrates.
All these alterations impact the entire importance chain and that includes details service providers inside the field. Eurasia Photodiode semiconductor has been delivering information and facts to the global photodiode semiconductor market in excess of twenty five years. The adjustments from the international business signifies EuroAsia Photodiode semiconductor will yet again relocate in accordance with the photodiode semiconductor sector as it enters the following dynamic period of worldwide development. Silicon Photodiode semiconductor could be the new reputation for our name highlighting the easy actuality from the progressive engineering and manufacturing that identifies this world-wide business. The photodiode semiconductor market is tipped for powerful growth across the following few years and Silicon Photodiode semiconductor would be the essential information and facts portal for your world’s silicon photodiode semiconductor community, allowing positive interaction ways to foster advancement. The new headline also provides together our secure of titles, with the sister distribution Substance Photodiode semiconductor covering up production on substance material substrates.